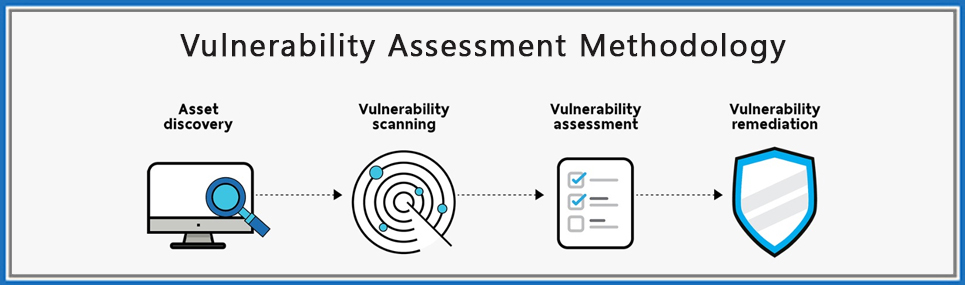
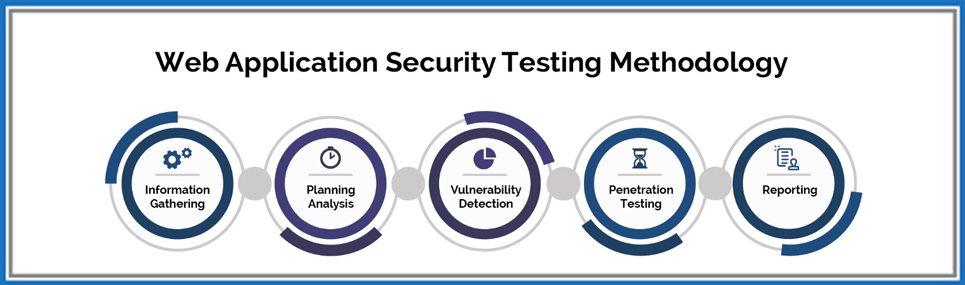
Vulnerability Assessment
Vulnerability analysis is a process to identify the threats, risks, and lacking in the systems, web technologies, network, cloud, IOT, and many more.
Vulnerability Management can be defined as “the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities. “Organizations use vulnerability management to pre-emptively defend against the exploitation of vulnerabilities in company applications, software, and networks. Organizations that can effectively implement vulnerability management will be significantly safer from data breaches and theft.